10+ Electronic money laundering is a form of information piracy ideas
Home » about money loundering idea » 10+ Electronic money laundering is a form of information piracy ideasYour Electronic money laundering is a form of information piracy images are available in this site. Electronic money laundering is a form of information piracy are a topic that is being searched for and liked by netizens now. You can Find and Download the Electronic money laundering is a form of information piracy files here. Find and Download all royalty-free photos.
If you’re searching for electronic money laundering is a form of information piracy images information connected with to the electronic money laundering is a form of information piracy topic, you have visit the ideal site. Our website frequently gives you suggestions for seeking the maximum quality video and image content, please kindly hunt and locate more informative video articles and images that fit your interests.
Electronic Money Laundering Is A Form Of Information Piracy. Ad Save Time Signing Sending Documents Online. Criminals use a wide variety of money laundering techniques to make illegally obtained. Add Signature Fields Collect eSignatures. By its very nature money laundering is an illegal activity carried out by criminals which occurs outside of the normal range of economic and financial statistics.
 Fraud And Electronic Money Laundering Ppt Video Online Download From slideplayer.com
Fraud And Electronic Money Laundering Ppt Video Online Download From slideplayer.com
Ad Save Time Signing Sending Documents Online. The Money Laundering Terrorist Financing and Transfer of Funds Information on the Payer Regulations 2017 require appropriate identity ID evidence to be provided when certain transactions take. EU Directives on Money Laundering. IMoLIN is an Internet-based network assisting governments organizations and individuals in the fight against illicit financial flows money laundering and the financing of terrorism. Money laundering is the illegal process of making dirty money appear legitimate instead of ill-gotten. Add Signature Fields Collect eSignatures.
B The prosecution of any offense or violation under this Act shall proceed independently of any proceeding relating to the unlawful activity SEC.
Placement layering and integration. Any person who with malice or in bad faith report or files a completely unwarranted or false information relative to money laundering transaction against any person shall be subject to a penalty of six 6 months to four 4 years imprisonment and a fine of not less than One hundred thousand Philippine pesos Php10000000 but not more than Five hundred thousand Philippine pesos. Ad Save Time Signing Sending Documents Online. Electronic money laundering is a form of information piracy. There are several denominations used in international law as tra nslations for the expression. To disguise illicit profits without compromising those involved money laundering takes place through a dynamic process that requires.
 Source: slideplayer.com
Source: slideplayer.com
B The prosecution of any offense or violation under this Act shall proceed independently of any proceeding relating to the unlawful activity SEC. Any person who with malice or in bad faith report or files a completely unwarranted or false information relative to money laundering transaction against any person shall be subject to a penalty of six 6 months to four 4 years imprisonment and a fine of not less than One hundred thousand Philippine pesos Php10000000 but not more than Five hundred thousand Philippine pesos. IMoLIN is an Internet-based network assisting governments organizations and individuals in the fight against illicit financial flows money laundering and the financing of terrorism. Add Signature Fields Collect eSignatures. There are three main stages of crypto money laundering.
 Source: businessyield.com
Source: businessyield.com
Piracy kidnapping illegal restraint and hostage-taking fall under the Financial Action Task Forces FATFs categories of designated serious offences for money laundering. Electronic money laundering is a form of information piracy. The methods by which money may be laundered are varied and can range in sophistication. Ad Save Time Signing Sending Documents Online. Piracy kidnapping illegal restraint and hostage-taking fall under the Financial Action Task Forces FATFs categories of designated serious offences for money laundering.
Source:
IMoLIN is an Internet-based network assisting governments organizations and individuals in the fight against illicit financial flows money laundering and the financing of terrorism. Money laundering is the illegal process of making dirty money appear legitimate instead of ill-gotten. Start Working with Your Docs. Start Working with Your Docs. Placement layering and integration.
 Source: researchgate.net
Source: researchgate.net
Along with some other aspects of underground economic activity rough estimates have been put forward to give some sense of the scale of the problem. Start Working with Your Docs. By its very nature money laundering is an illegal activity carried out by criminals which occurs outside of the normal range of economic and financial statistics. Placement layering and integration. Criminals use a wide variety of money laundering techniques to make illegally obtained.
Source:
- first distancing funds from their source avoiding an association direct them with the crime. The Achilles Heel Bibliography and some useful links Methods and Stages of Money Laundering. Transcending the illusory barriers. To the International Money Laundering Information Network. Electronic money laundering is a form of information piracy.
 Source: pinterest.com
Source: pinterest.com
Add Signature Fields Collect eSignatures. - second the disguise of its various movements to hinder the tracing of these resources. The anti-money laundering policy ensures the required attention is paid to a client in order to establish whether or not the bank wants to do business with the client and that the banks clients are of good reputation In the policy of Piraeus Bank AD Beograd there is a special program Know Your Customer. Ad Save Time Signing Sending Documents Online. Add Signature Fields Collect eSignatures.
 Source: slideplayer.com
Source: slideplayer.com
- second the disguise of its various movements to hinder the tracing of these resources. Along with some other aspects of underground economic activity rough estimates have been put forward to give some sense of the scale of the problem. Previous Object attributes are often called ____ to help distinguish them from other variables you might use. Add Signature Fields Collect eSignatures. Start Working with Your Docs.
Source:
The same concepts that apply to money laundering using cash apply to money laundering using cryptocurrencies. Start Working with Your Docs. There are three stages involved in money laundering. Previous Object attributes are often called ____ to help distinguish them from other variables you might use. Start Working with Your Docs.
 Source: slideplayer.com
Source: slideplayer.com
Ad Save Time Signing Sending Documents Online. Electronic money laundering is a form of information piracy. Along with some other aspects of underground economic activity rough estimates have been put forward to give some sense of the scale of the problem. Start Working with Your Docs. Add Signature Fields Collect eSignatures.
 Source: pinterest.com
Source: pinterest.com
The Money Laundering Terrorist Financing and Transfer of Funds Information on the Payer Regulations 2017 require appropriate identity ID evidence to be provided when certain transactions take. The anti-money laundering policy ensures the required attention is paid to a client in order to establish whether or not the bank wants to do business with the client and that the banks clients are of good reputation In the policy of Piraeus Bank AD Beograd there is a special program Know Your Customer. Get Started for Free. The Achilles Heel Bibliography and some useful links Methods and Stages of Money Laundering. Placement layering and integration.
 Source: in.pinterest.com
Source: in.pinterest.com
To disguise illicit profits without compromising those involved money laundering takes place through a dynamic process that requires. To the International Money Laundering Information Network. To disguise illicit profits without compromising those involved money laundering takes place through a dynamic process that requires. Placement layering and integration. There are three main stages of crypto money laundering.
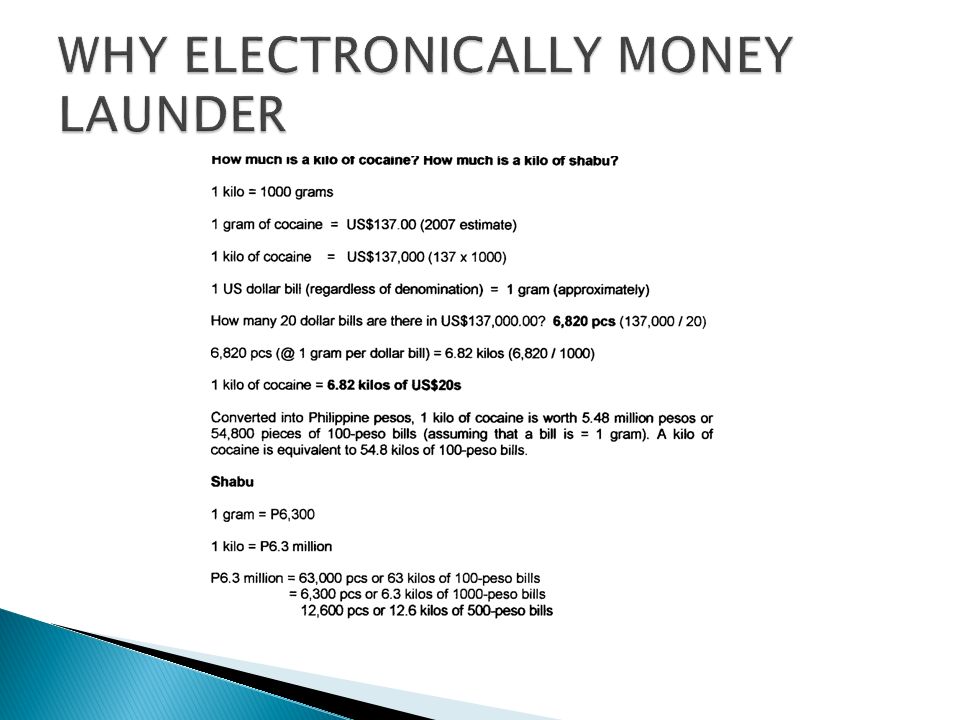 Source: slideplayer.com
Source: slideplayer.com
Previous Object attributes are often called ____ to help distinguish them from other variables you might use. Money laundering is the process by which the proceeds of the crime and the true ownership of those proceeds are concealed or made opaque so that the proceeds appear to come from a legitimate source. There are three main stages of crypto money laundering. Previous Object attributes are often called ____ to help distinguish them from other variables you might use. Transcending the illusory barriers.
 Source: slideplayer.com
Source: slideplayer.com
Money laundering is the process by which the proceeds of the crime and the true ownership of those proceeds are concealed or made opaque so that the proceeds appear to come from a legitimate source. The Money Laundering Terrorist Financing and Transfer of Funds Information on the Payer Regulations 2017 require appropriate identity ID evidence to be provided when certain transactions take. IMoLIN is an Internet-based network assisting governments organizations and individuals in the fight against illicit financial flows money laundering and the financing of terrorism. Money laundering refers to the process of concealing the source of illegally obtained money. Money laundering is the process by which the proceeds of the crime and the true ownership of those proceeds are concealed or made opaque so that the proceeds appear to come from a legitimate source.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title electronic money laundering is a form of information piracy by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.
Category
Related By Category
- 13++ Bank negara malaysia ditubuhkan pada info
- 13+ Different meaning of money laundering ideas
- 20++ Anti money laundering training games ideas in 2021
- 20++ Federal money laundering statute information
- 10+ Def of money laundering ideas
- 10++ Banking secrecy in singapore info
- 20+ Financial crime risk layering information
- 15+ Bank secrecy act high risk businesses information
- 13+ Fca authorisation application forms info
- 13++ Certified anti money laundering specialist certification information