14+ How do criminals often attempt to avoid detection in the first stage of info
Home » about money loundering Info » 14+ How do criminals often attempt to avoid detection in the first stage of infoYour How do criminals often attempt to avoid detection in the first stage of images are ready in this website. How do criminals often attempt to avoid detection in the first stage of are a topic that is being searched for and liked by netizens now. You can Get the How do criminals often attempt to avoid detection in the first stage of files here. Download all free images.
If you’re looking for how do criminals often attempt to avoid detection in the first stage of pictures information related to the how do criminals often attempt to avoid detection in the first stage of topic, you have come to the right site. Our website frequently provides you with suggestions for seeking the maximum quality video and picture content, please kindly hunt and locate more enlightening video articles and images that fit your interests.
How Do Criminals Often Attempt To Avoid Detection In The First Stage Of. Anti-virus scanner sounds an alarm if the device has a virus scanner it can detect ransomware infection early unless it has been bypassed. The placement stage represents the initial entry of the dirty cash or proceeds of crime into the financial system. For instance many criminal groups use. The stages of money laundering include the.
 Disorder Policing To Reduce Crime A Systematic Review Braga 2019 Campbell Systematic Reviews Wiley Online Library From onlinelibrary.wiley.com
Disorder Policing To Reduce Crime A Systematic Review Braga 2019 Campbell Systematic Reviews Wiley Online Library From onlinelibrary.wiley.com
Conceal their presence and mask activity to avoid detection and thwart the inevitable investigation. This might mean wiping files and metadata overwriting data with false timestamps timestomping and misleading information or modifying critical information so that it looks like the data was never touched. For example if the organization owns a restaurant it might inflate the daily cash. It may be used to convince the examinee that the polygraph instrument will detect any deception. Placement is the first stage in money laundering where the cash proceeds of criminal activity enter into the financial system. This process often involves a demonstration in which the examinee is asked to lie about an unimportant matter and the examiner shows the instruments ability to detect the lie.
The Classical School defined crime in legal.
How Do Criminals Often Attempt To Avoid Detection In The First Stage Of The idea of money laundering is essential to be understood for these working within the financial sector. Criminals may use multiple professionals to further complicate the money laundering process in an effort to avoid detection. If this extension has changed to an unfamiliar combination of. First they elect people to represent them in making laws and indirectly in enforcing them. Placement is the first stage in money laundering where the cash proceeds of criminal activity enter into the financial system. 4 In comparison question testing the interview is also.
 Source: law.lclark.edu
Source: law.lclark.edu
Sexual abuse can be more easily committed without detection van Dam 2006. First a hacker may gain valuable access to a single account through a successful phishing attempt. Veloped in the eighteenth century in an attempt to reform the legal system and to protect the accused against harsh and arbitrary action on the part of the State. The modus operandi or method used by a criminal to commit an offense sometimes helps to identify the suspect as many offenders repeatedly commit offenses in similar ways. This process often involves a demonstration in which the examinee is asked to lie about an unimportant matter and the examiner shows the instruments ability to detect the lie.
 Source: onlinelibrary.wiley.com
Source: onlinelibrary.wiley.com
The stages of money laundering include the. The known methods used are. It may be used to convince the examinee that the polygraph instrument will detect any deception. And b it places the money into the legitimate. Cyber-attackers do the same thing.
 Source: pinterest.com
Source: pinterest.com
A it relieves the criminal of holding and guarding large amounts of bulky of cash. Generally this stage serves two purposes. This is done so that they can get rid of the cash that is derived from criminal sources. Veloped in the eighteenth century in an attempt to reform the legal system and to protect the accused against harsh and arbitrary action on the part of the State. Citizens play many roles Lacey 1994.
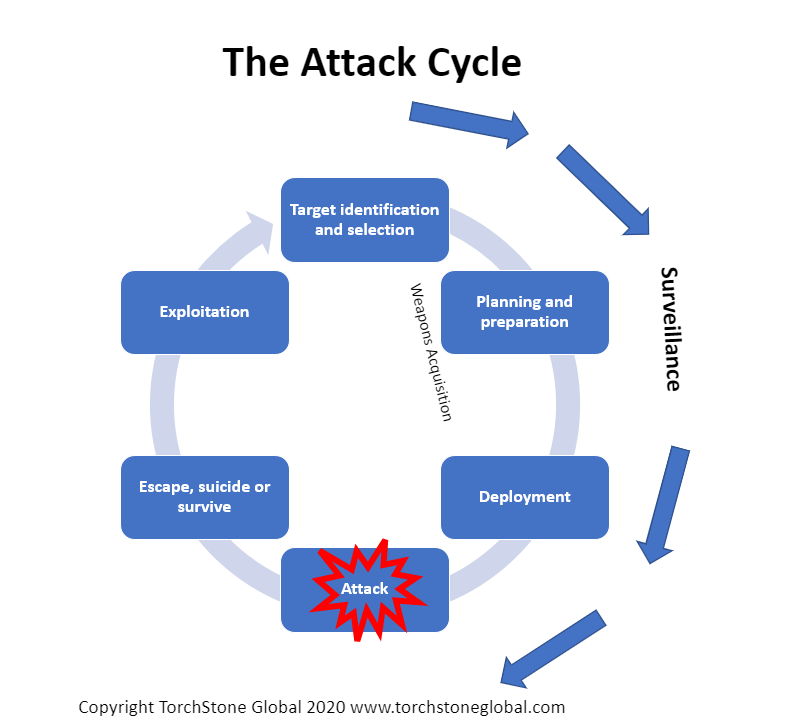 Source: torchstoneglobal.com
Source: torchstoneglobal.com
Property Dealing The sale of property to integrate laundered money back into the economy is a common practice amongst criminals. Its a course of by which dirty money is transformed into clean money. How do you know if your computer is infected. Anti-virus scanner sounds an alarm if the device has a virus scanner it can detect ransomware infection early unless it has been bypassed. A burglars method of entry into a house the type of property stolen or the kind of deception practiced on the victim of a fraud all may suggest who was responsible for a crime.
Source:
Cyber-attackers do the same thing. This is most critical stage for any money launderer as the criminal can effectively mask his illegal funds by combining his clean funds and create an. When attempts at denial do not succeed a guilty suspect often makes objections to support a claim of innocence eg I would never do that because I love my job The investigator should generally accept these objections as if they were truthful rather than arguing with the suspect and use the objections to further develop the theme. Here are some ways to detect a ransomware attack. Veloped in the eighteenth century in an attempt to reform the legal system and to protect the accused against harsh and arbitrary action on the part of the State.
 Source: pressbooks.bccampus.ca
Source: pressbooks.bccampus.ca
British data suggest that over 75. The infected images were accessed more then two million times and. Money laundering is often comprised of a number of stages including. A it relieves the criminal of holding and guarding large amounts of bulky of cash. For instance many criminal groups use.
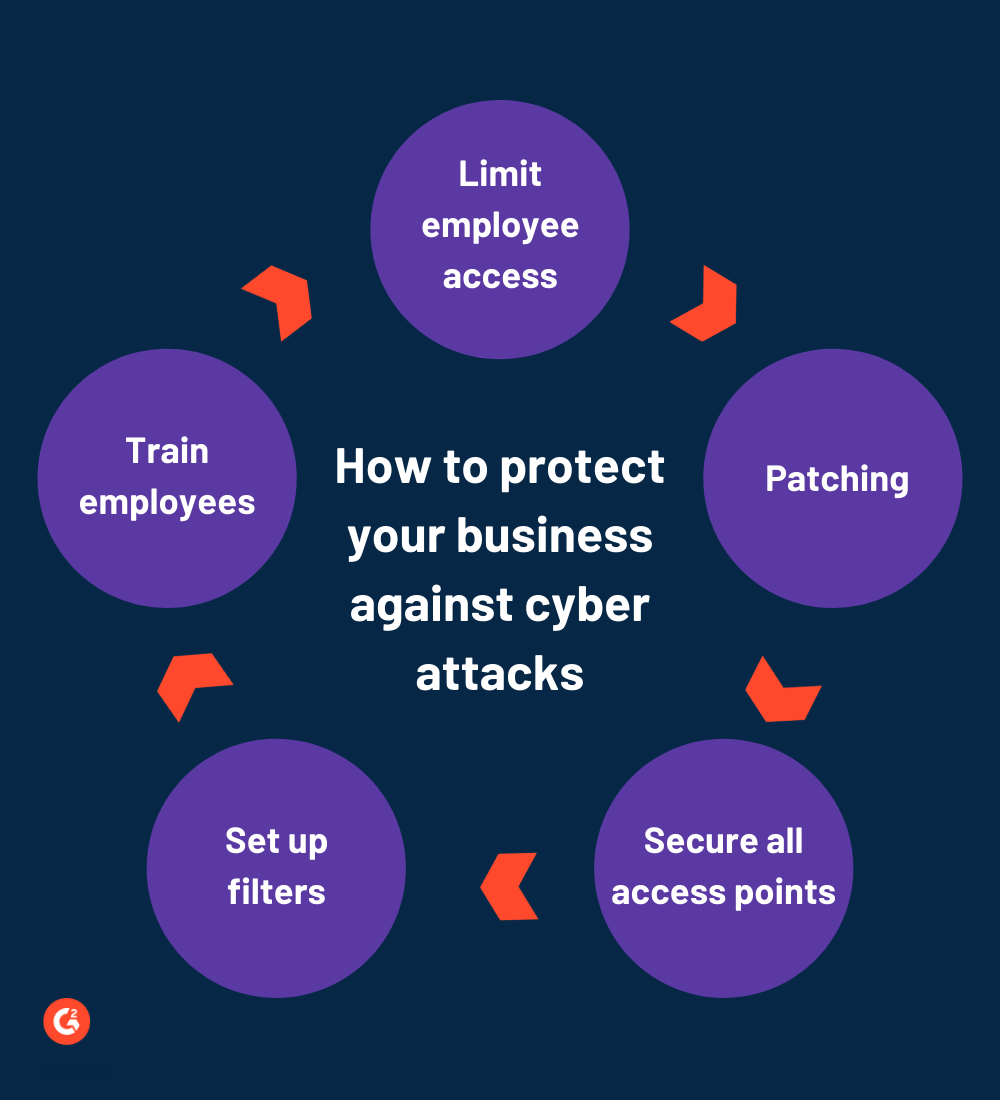 Source: g2.com
Source: g2.com
Sexual abuse can be more easily committed without detection van Dam 2006. Secondly and most crucially they play a substantial role more so than the police in detecting and reporting crime. Disorganized criminals may be young under the influence of alcohol or drugs or mentally ill. Cyber-attackers do the same thing. Its a course of by which dirty money is transformed into clean money.
 Source:
Source:
Veloped in the eighteenth century in an attempt to reform the legal system and to protect the accused against harsh and arbitrary action on the part of the State. If this extension has changed to an unfamiliar combination of. This process often involves a demonstration in which the examinee is asked to lie about an unimportant matter and the examiner shows the instruments ability to detect the lie. How Do Criminals Often Attempt To Avoid Detection In The First Stage Of The idea of money laundering is essential to be understood for these working within the financial sector. The infected images were accessed more then two million times and.
 Source: mdpi.com
Source: mdpi.com
If this extension has changed to an unfamiliar combination of. This might mean wiping files and metadata overwriting data with false timestamps timestomping and misleading information or modifying critical information so that it looks like the data was never touched. Placement is the first stage in money laundering where the cash proceeds of criminal activity enter into the financial system. 4 In comparison question testing the interview is also. Check file extension for example the normal extension of an image file is jpg.
Conceal their presence and mask activity to avoid detection and thwart the inevitable investigation. And b it places the money into the legitimate. It may be used to convince the examinee that the polygraph instrument will detect any deception. Property Dealing The sale of property to integrate laundered money back into the economy is a common practice amongst criminals. The infected images were accessed more then two million times and.
 Source: mdpi.com
Source: mdpi.com
Placing the cryptomining code within a Docker image helps avoid detection. Anti-virus scanner sounds an alarm if the device has a virus scanner it can detect ransomware infection early unless it has been bypassed. The modus operandi or method used by a criminal to commit an offense sometimes helps to identify the suspect as many offenders repeatedly commit offenses in similar ways. This might mean wiping files and metadata overwriting data with false timestamps timestomping and misleading information or modifying critical information so that it looks like the data was never touched. Veloped in the eighteenth century in an attempt to reform the legal system and to protect the accused against harsh and arbitrary action on the part of the State.
 Source: shuftipro.com
Source: shuftipro.com
For instance many criminal groups use. Here are some ways to detect a ransomware attack. When attempts at denial do not succeed a guilty suspect often makes objections to support a claim of innocence eg I would never do that because I love my job The investigator should generally accept these objections as if they were truthful rather than arguing with the suspect and use the objections to further develop the theme. They strategically manipulate the victim their family and the community to hide their deviant intentions and avoid detection. This is most critical stage for any money launderer as the criminal can effectively mask his illegal funds by combining his clean funds and create an.
 Source: mdpi.com
Source: mdpi.com
Child molesters who groom often do so while keeping a guise of being kind charming and helpful van Dam 2001. How do you know if your computer is infected. And b it places the money into the legitimate. This is most critical stage for any money launderer as the criminal can effectively mask his illegal funds by combining his clean funds and create an. 4 In comparison question testing the interview is also.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title how do criminals often attempt to avoid detection in the first stage of by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.
Category
Related By Category
- 15+ Handwritten declaration for bank po information
- 16+ Anti money laundering news 2021 information
- 12++ Definition of launder money information
- 20+ Bank negara malaysia undergraduate scholarship ideas in 2021
- 11+ Anti money laundering test questions and answers pdf information
- 17++ 3 elements of money laundering ideas
- 19++ Anti money laundering and counter terrorism financing act 2006 information
- 18+ Eso laundering meaning ideas
- 12+ Credit union bank secrecy act policy ideas in 2021
- 18+ How serious is money laundering ideas